A vulnerability in a number of variations of OxygenOS, the Android-based working system from OnePlus, permits any put in app to entry SMS knowledge and metadata with out requiring permission or consumer interplay.
OnePlus, a subsidiary of Oppo, is a Shenzhen-based shopper electronics maker identified for growing high-end smartphones at aggressive pricing. Whereas different main Chinese language manufacturers like Huawei and Xiaomi aren’t obtainable within the U.S., OnePlus gadgets are formally obtainable within the nation.
The flaw, tracked as CVE-2025-10184, and found by Rapid7 researchers, is at the moment unpatched and exploitable. The Chinese language OEM failed to reply to Rapid7’s disclosures to today, and the cybersecurity firm printed the technical particulars together with a proof-of-concept (PoC) exploit.
Supply of the issue
The issue arises from OnePlus altering the inventory Android Telephony bundle to introduce further exported content material suppliers like PushMessageProvider, PushShopProvider, and ServiceNumberProvider.
The manifest for these suppliers doesn’t declare a write permission for ‘READ_SMS,’ leaving it open to any app by default, even those who don’t have SMS permissions.
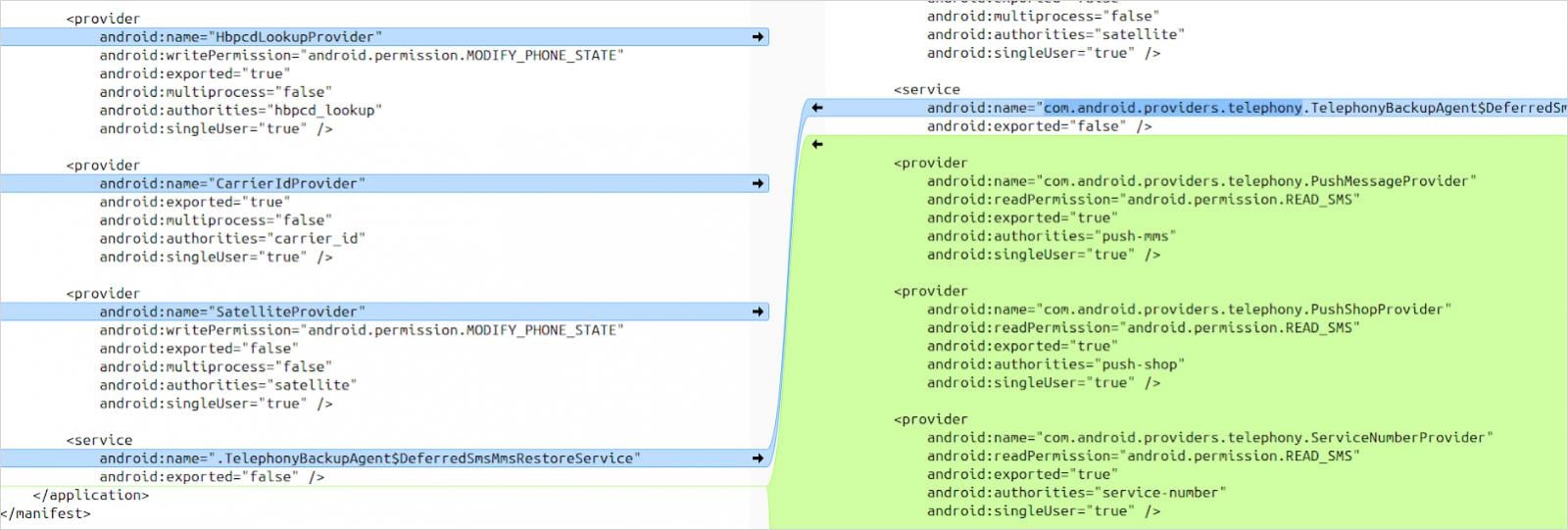
Supply: Rapid7
To make issues worse, client-supplied inputs aren’t sanitized, permitting “blind SQL injection” that would reconstruct SMS content material from the system database, bruteforcing it one character at a time.
“By utilizing an algorithm to repeat this course of for every character in every row returned by the sub question, it’s attainable to exfiltrate the database content material, utilizing the return worth from the replace technique as an indicator of true/false,” describes Rapid7 within the report.
So, whereas the learn permission for SMS is accurately set, the write permission isn’t, permitting the inference of SMS content material when sure stipulations are met:
- Uncovered desk should already comprise at the least one row, so replace() can return a non-zero “rows modified” end result.
- The supplier should enable insert() so an attacker can create a dummy row to function on if the desk is empty.
- The sms desk should be in the identical SQLite database file as a result of the injected subquery should be capable of reference it.
Supply: Rapid7
Affect and response
The problem impacts all variations of OxygenOS from 12 to the newest one, which is 15, which is the newest, constructed on prime of Android 15.
Rapid7 researchers examined and confirmed vulnerability on OnePlus 8T and 10 Professional, working numerous OxygenOS variations and Telephony bundle numbers, however famous that their record is nearly undoubtedly non-exhaustive.
“Whereas the construct numbers above [on the table] are particular to the take a look at gadgets, as the difficulty impacts a core element of Android, we anticipate this vulnerability to have an effect on different OnePlus gadgets working the above variations of OxygenOS, i.e., it doesn’t appear to be a hardware-specific problem,” defined Rapid7.
| Gadget / Mannequin | Package deal model | OxygenOS model | Construct Quantity |
| OnePlus 8T / KB2003 | 3.4.135 | 12 | KB2003_11_C.3 |
| OnePlus 10 Professional 5G / NE2213 | 14.10.30 | 14 | NE2213_14.0.0.700(EX01) |
| OnePlus 10 Professional 5G / NE2213 | 15.30.5 | 15 | NE2213_15.0.0.502(EX01) |
| OnePlus 10 Professional 5G / NE2213 | 15.30.10 | 15 | NE2213_15.0.0.700(EX01) |
| OnePlus 10 Professional 5G / NE2213 | 15.40. | 15 | NE2213_15.0.0.901(EX01) |
The researchers tried to contact OnePlus to share their findings on Could 1 and adopted up on different e-mail addresses a number of occasions till August 16.
After receiving no response to seven separate communication makes an attempt, the safety agency publicly disclosed the main points for CVE-2025-10184.
Shortly after publication of Rapid7’s report, OnePlus acknowledged the disclosure and stated they’ve launched an investigation into the issue.
BleepingComputer has contacted OnePlus to request a remark, however we’re nonetheless awaiting a response.
Till a patch is made obtainable, it is strongly recommended to maintain the variety of put in apps in your OnePlus system to a minimal, solely belief respected publishers, and change from SMS-based two-factor authentication to OTP apps like Google Authenticator.
Since SMS isn’t correctly remoted on OnePlus gadgets, delicate communications ought to solely happen on end-to-end encrypted apps.



