North Korean menace actors are utilizing new malware known as OtterCookie within the Contagious Interview marketing campaign that’s focusing on software program builders.
Contagious Interview has been energetic since at the least December 2022, in accordance with researchers at cybersecurity firm Palo Alto Networks. The marketing campaign targets software program builders with faux job provides to ship malware resembling BeaverTail and InvisibleFerret.
A report from NTT Safety Japan notes that the Contagious Interview operation is now utilizing a brand new piece of malware known as OtterCookie, which was seemingly launched in September and with a brand new variant showing within the wild in November.
OtterCookie assault chain
Similar to within the assaults documented by Palo Alto Networks’ Unit42 researchers, OtterCookie is delivered through a loader that fetches JSON knowledge and executes the ‘cookie’ property as JavaScript code.
NTT says that, regardless that BeaverTail stays the most typical payload, OtterCookie has been seen in some circumstances both deployed alongside BeaverTail or by itself.
The loader infects targets by Node.js tasks or npm packages downloaded from GitHub or Bitbucket. Nevertheless, recordsdata constructed as Qt or Electron functions had been additionally used not too long ago.
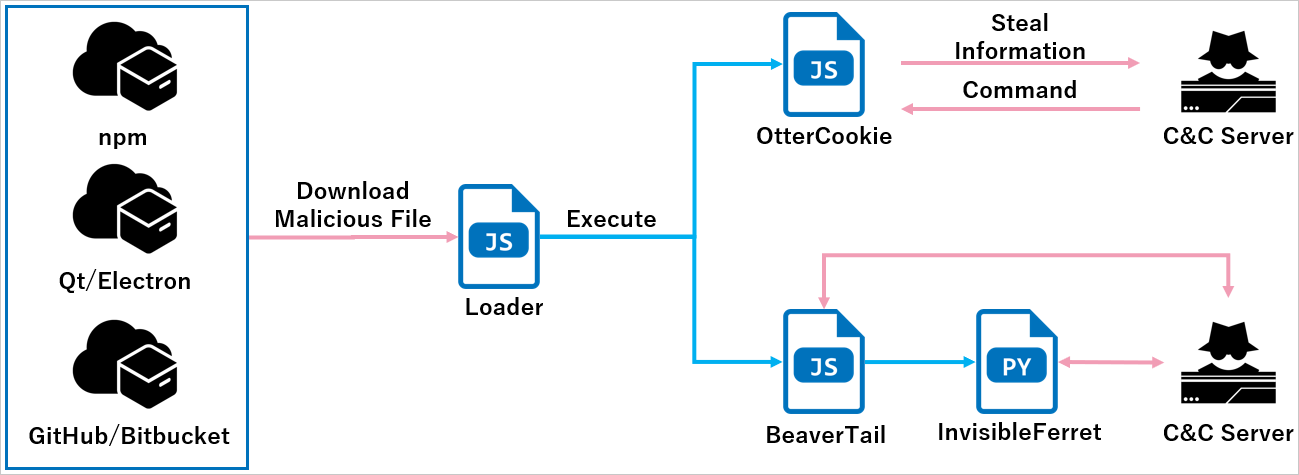
Supply: NTT Japan
As soon as energetic on the goal gadget, OtterCookie establishes safe communications with its command and management (C2) infrastructure utilizing the Socket.IO WebSocket instrument, and awaits for instructions.
The researchers noticed shell instructions that carry out knowledge theft (e.g. amassing cryptocurrency pockets keys, paperwork, photos, and different useful data).
“The September model of OtterCookie already included a built-in performance to steal keys associated to cryptocurrency wallets,” NTT explains.
“For instance, the checkForSensitiveData perform used common expressions to verify for Ethereum personal keys,” the researchers word, including that this was modified with the November variant of the malware the place that is achieved by distant shell instructions.
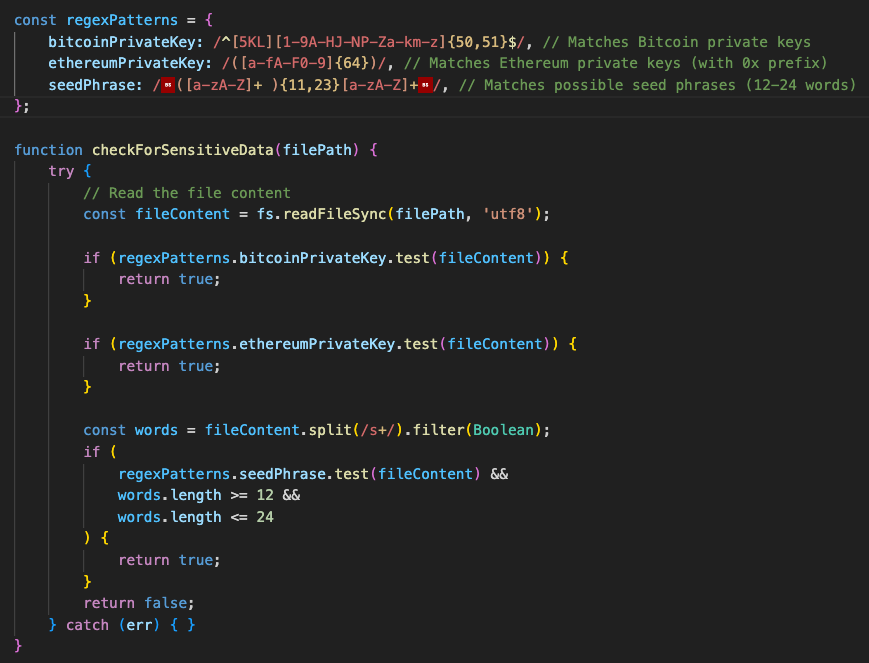
Supply: NTT Japan
The newest model of OtterCookie can even exfiltrate clipboard knowledge to the menace actors, which can comprise delicate data.
Instructions usually used for reconnaissance, like ‘ls’ and ‘cat’, had been additionally detected, indicating the attacker’s intention to discover the setting and stage it for deeper infiltration or lateral motion.
The looks of latest malware and the diversification of the an infection strategies point out that the menace actors behind the Contagious Interview marketing campaign experiment with new techniques.
Software program builders ought to attempt to confirm details about a possible employer and be cautious of working code on private or work computer systems as a part of a job provide that require coding assessments.


