A member of the Loopy ransomware gang is abusing official worker monitoring software program and the SimpleHelp distant assist instrument to keep up persistence in company networks, evade detection, and put together for ransomware deployment.
The breaches had been noticed by researchers at Huntress, who investigated a number of incidents the place menace actors deployed Internet Monitor for Workers Skilled alongside SimpleHelp for distant entry to a breached community, whereas mixing in with regular administrative exercise.
In a single intrusion, attackers put in Internet Monitor for Workers Skilled utilizing the Home windows Installer utility, msiexec.exe, permitting them to deploy the monitoring agent on compromised methods immediately from the developer’s website.
As soon as put in, the instrument allowed attackers to remotely view the sufferer’s desktop, switch recordsdata, and execute instructions, successfully offering full interactive entry to compromised methods.
The attackers additionally tried to allow the native administrator account utilizing this command:
web consumer administrator /energetic:sure
For redundant persistence, attackers downloaded and put in the SimpleHelp distant entry consumer by way of PowerShell instructions, utilizing file names just like the official Visible Studio vshost.exe.
The payload was then executed, permitting attackers to keep up distant entry even when the worker monitoring instrument was eliminated.
The SimpleHelp binary was generally disguised utilizing filenames that pretended to be associated to OneDrive:
C:ProgramDataOneDriveSvcOneDriveSvc.exe
The attackers used the monitoring software program to execute instructions remotely, switch recordsdata, and monitor system exercise in actual time.
Researchers additionally noticed the attackers disabling Home windows Defender by making an attempt to cease and delete related providers.
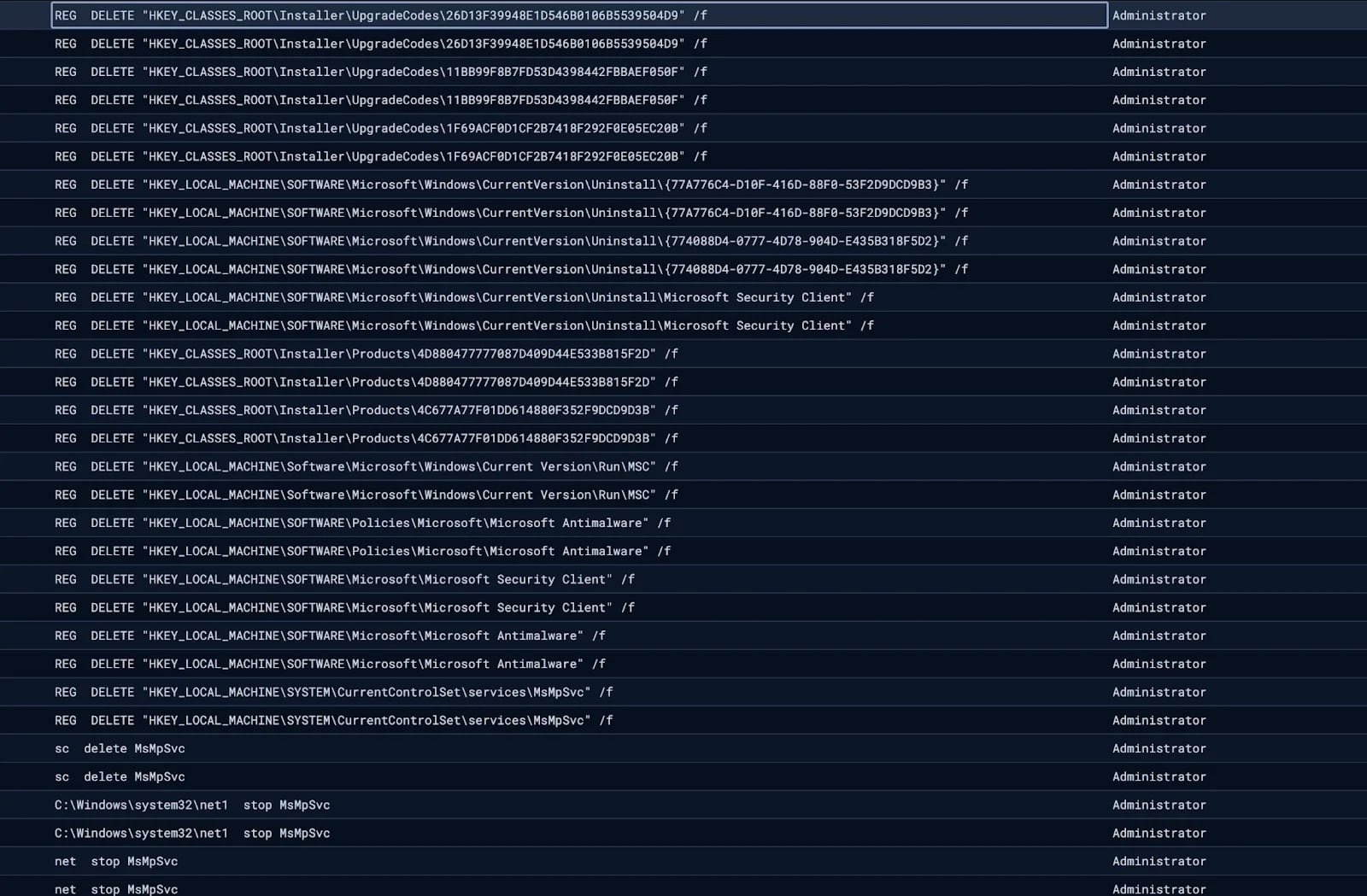
Supply: Huntress
In a single incident, the hackers configured monitoring guidelines in SimpleHelp to alert them when units accessed cryptocurrency wallets or had been utilizing distant administration instruments as they ready for ransomware deployment and potential cryptocurrency theft.
“The logs present the agent constantly biking by means of set off and reset occasions for cryptocurrency-related key phrases, together with pockets providers (metamask, exodus, pockets, blockchain), exchanges (binance, bybit, kucoin, bitrue, poloniex, bc.sport, noones), blockchain explorers (etherscan, bscscan), and the fee platform payoneer,” explains Huntress.
“Alongside these, the agent additionally monitored for distant entry instrument key phrases, together with RDP, anydesk, ultraview, teamview, and VNC, more likely to detect if anybody was actively connecting to the machine.”
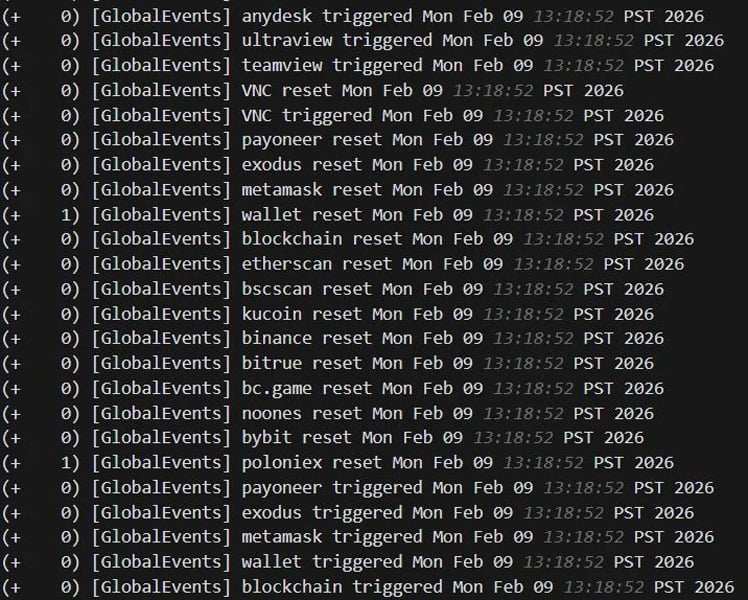
Supply: Huntress
The usage of a number of distant entry instruments offered redundancy for the attackers, guaranteeing they retained entry even when one instrument was found or eliminated.
Whereas just one incident led to the deployment of Loopy ransomware, Huntress believes the identical menace actor is behind each incidents.
“The identical filename (vhost.exe) and overlapping C2 infrastructure had been reused throughout each circumstances, strongly suggesting a single operator or group behind each intrusions,” explains Huntress.
The usage of official distant administration and monitoring instruments has change into more and more frequent in ransomware intrusions, as these instruments permit attackers to mix in with official community visitors.
Huntress warns that organizations ought to intently monitor for unauthorized installations of distant monitoring and assist instruments.
Moreover, as each breaches had been enabled by means of compromised SSL VPN credentials, organizations must implement MFA on all distant entry providers used to entry the community.
Trendy IT infrastructure strikes quicker than handbook workflows can deal with.
On this new Tines information, learn the way your group can scale back hidden handbook delays, enhance reliability by means of automated response, and construct and scale clever workflows on prime of instruments you already use.




