What simply occurred? Tons of of GitHub repositories providing Minecraft mods have grow to be the newest battleground in a classy malware marketing campaign, concentrating on the sport’s huge and artistic participant group. On the coronary heart of this operation is the Stargazers Ghost Community, an elaborate cybercriminal infrastructure uncovered by Examine Level Analysis.
Not like typical malware campaigns, Stargazers Ghost Community is a distribution-as-a-service operation that leverages hundreds of pretend GitHub accounts to unfold malicious software program disguised as legit mods and cheat instruments. This operation makes use of GitHub’s trusted platform to distribute malicious Java archives, evading detection whereas compromising over 1,500 units since March 2025.
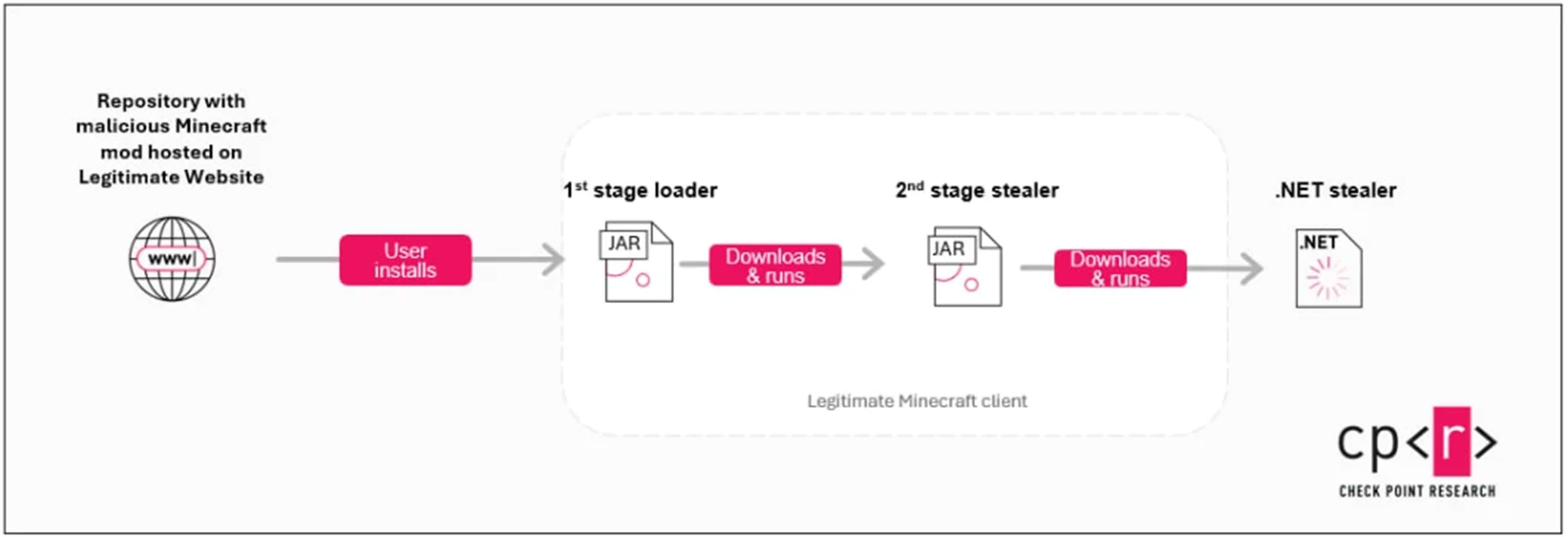
The assault begins when gamers set up counterfeit mods, typically in pursuit of gameplay benefits. These JAR information – designed as Minecraft Forge mods – activate solely when the sport launches, instantly deploying anti-analysis defenses. The loader checks for digital machines, safety instruments like Wireshark, and community screens, terminating itself if detected to bypass automated sandboxes.
Upon passing these checks, it retrieves a Base64-encoded Pastebin URL that factors to a second-stage Java stealer hosted on attacker-controlled IP addresses. This intermediate payload particularly targets authentication tokens from Minecraft’s official and third-party launchers, whereas concurrently harvesting Discord and Telegram session knowledge. The stolen credentials are transmitted through HTTP POST requests to command-and-control servers.
The an infection escalates as this stealer downloads and executes “44 CALIBER” – a .NET-based last payload. Recognized in its meeting metadata and that includes Russian-language copyright messages like “F*ckTheSystem Copyright © 2021,” this superior stealer targets browser credentials, cryptocurrency wallets, VPN configurations, and information saved within the Desktop and Paperwork folders. It captures screenshots, clipboard contents, and system metadata earlier than exfiltrating every part by way of Discord webhooks.
Proof factors to Russian-speaking operators behind the Stargazers Ghost Community, with UTC+3 timestamps on malicious commits, Russian feedback embedded within the code, and package deal names that reference Lake Baikal in Siberia all supporting this conclusion.
Faux “stars” from roughly 70 accounts make malicious mods seem legit, whereas Pastebin hit counters counsel not less than 1,500 profitable infections. Financially motivated, the group has reportedly earned as much as $8,000 month-to-month, with whole earnings probably reaching $100,000.
Minecraft’s participant base – over 200 million month-to-month customers, with the bulk beneath age 21 or of their early 20s – makes it a high-value goal. Younger gamers in search of unofficial enhancements typically overlook safety dangers, whereas the malware’s Java basis permits it to evade conventional antivirus scans.
As new repositories emerge day by day, specialists urge gamers to supply mods completely from vetted platforms like CurseForge. Examine Level Analysis continues to observe the Stargazers Ghost Community, with ongoing investigations revealing new an infection vectors.