A brand new model of the Banshee info-stealing malware for macOS has been evading detection over the previous two months by adopting string encryption from Apple’s XProtect.
Banshee is an info stealer targeted on macOS techniques. It emerged in mid-2024 as a stealer-as-a-service obtainable to cybercriminals for $3,000.
Its supply code was leaked on the XSS boards in November 2024, resulting in the challenge shutting down for the general public and creating a possibility for different malware builders to enhance on it.
Based on Test Level Analysis, which found one of many new variants, the encryption technique current in Banshee permits it to mix in with regular operations and to seem respectable whereas amassing delicate info from contaminated hosts.
One other change is that it not keep away from techniques belonging to Russian customers.
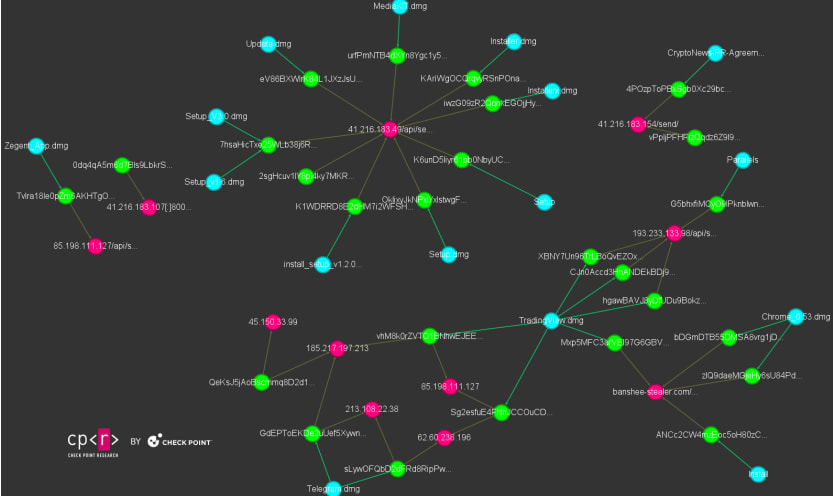
Supply: Test Level
XProtect encryption
Apple’s XProtect is the malware detection expertise constructed into macOS. It makes use of a algorithm, just like antivirus signatures, to determine and block identified malware.
The most recent model of Banshee Stealer adopted a string encryption algorithm that XProtect itself makes use of to guard its information.
By scrambling its strings and solely decrypting them throughout execution, Banshee can evade customary static detection strategies.
It is usually attainable that macOS and third-party anti-malware instruments deal with the actual encryption method with much less suspicion, permitting Banshee to function undetected for longer durations.
Stealing delicate information
The most recent Banshee stealer variant is primarily distributed through misleading GitHub repositories focusing on macOS customers by software program impersonation. The identical operators additionally goal Home windows customers, however with Lumma Stealer.
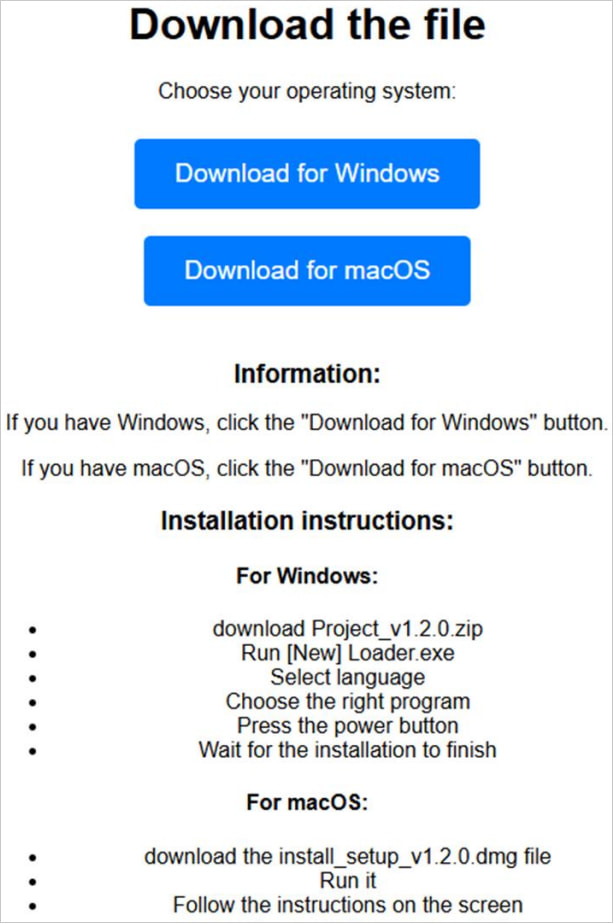
Supply: Test Level
Test Level studies that whereas the Banshee malware-as-a-service operation has remained down since November, a number of phishing campaigns continued to distribute the malware since the supply code leaked.
The infostealer targets information saved in fashionable browsers (e.g. Chrome, Courageous, Edge, and Vivaldi), together with passwords, two-factor authentication extensions, and cryptocurrency pockets extensions.
It additionally collects primary system and networking details about the host and serves victims misleading login prompts to steal their macOS passwords.


